The blockchain – Through Technology
Bitcoin and cryptocurrencies are exploding in popularity. You probably heard that the blockchain is the technology behind them but… What is the blockchain? How does it work?
Technology experts are claiming that the adoption of blockchain technologies will be as transcendental as the internet. If machine learning is disrupting labor, blockchain is disrupting society and economy.
Understanding the blockchain will allow you to see new perspectives, understand related concepts and will make you more comfortable to jump into the crypto world.
Good news is that you don’t need to be a computer scientist to grasp how the blockchain works. I will cover in this article the fundamentals leaving technical details aside.
We will focus on how the Bitcoin blockchain works for being the first and most important one.
What is the blockchain
The blockchain is a technology that creates an immutable distributed record. Imagine a book where you could write something pseudonymously that everyone could verify. This book can be replicated everywhere by anyone but no one can modify the book contents backwards.
Sounds complicated to achieve, in fact, it’s said to be one of the greatest recent computing science inventions. Blockchain technology is based on two pillars: cryptography and a consensus mechanism.
Cryptography allows the records to be secure and private. The consensus mechanism is a policy that allows to agree which data to add and how to the blockchain.
Cryptography
Cryptography is a set of techniques that allows secure communications. We can say a secure communication is one that is:
- Private – No one can read or listen to what we’re communicating.
- Immutable – No one can alter the message we’re sending.
Cryptography also is used to securely authenticate entities.
This concept is easy to understand but the techniques used are often based on hard mathematics. You don’t need to know them to understand the blockchain fundamentals.
Blockchains use these cryptographic techniques:
- Digital signatures
- Hash functions
- Merkle trees
- Timestamps
Digital signatures
A method is needed to validate the authenticity of the data transmitted in order to ensure who is the sender of the message. This is achieved using digital signatures which is the digital equivalent of the physical world ones.
Digital signatures are based on asymmetric cryptography. Each user have a set of two keys. One key is the private key and the other is the public key.
The private key must be preserved by the user and no one must have access to it. The public key can be shared with other users or systems to validate your signature authenticity.
To use a digital signature the user has to share its public key with one agent that the user want to communicate with. Then, the user has to sign its message by encrypting the message containing some information that identifies you1 using the private key. The agent can read your identity by decrypting the signature using your public key.
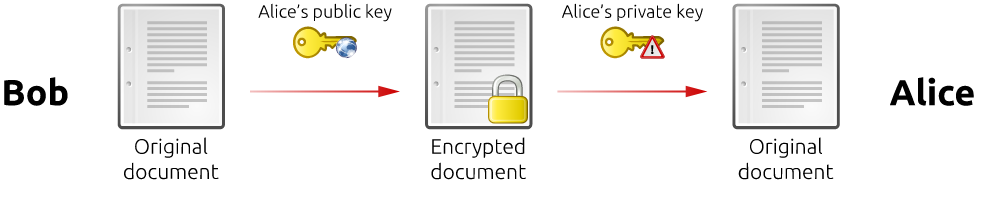
The keys have some properties that make them work only in one way. If you encrypt a message with the public key, only the private can decrypt it and vice-versa. This property guarantees that all communications can only be understood by the holder of the private key.
Signing, decrypting and its properties are based on hard mathematics.
With digital signatures now we have a secure method of identifying actors. Basically, your public key would act as your IBAN and the private key is your account password.
Hash functions
A hash function is a method that turns one input to a fixed sized value. Generally a string of characters or binary data. Hash functions are also known as digest functions as it mathematically summarizes the data into a fixed size value.
You can think of it like taking a photo. You’re creating a summarized version -a photo- of a real moment. The photo summarizes the reality in that moment. Similarly happens with hash functions and data.
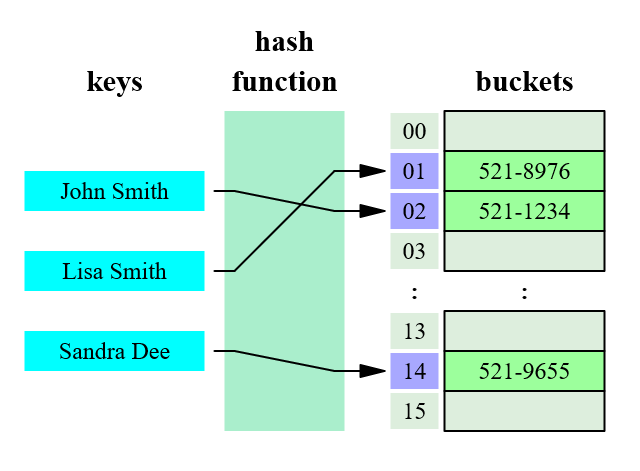
One important property of the hash functions is that you cannot guess the inputs from its output. You would need to try every possible input in order to reveal which was the input (bruteforcing).
Hash functions are used intensively in blockchains for multiple purposes:
- Summarizing a block.
- Generating Merkle trees (see below).
- Proof of work.
How hash functions works and how its properties are derived are also based on mathematics.
Merkle trees
A Merkle tree or hash tree is a type of hierarchical data structure that consists of linked parents and children nodes whose contents are the hashes of their children.
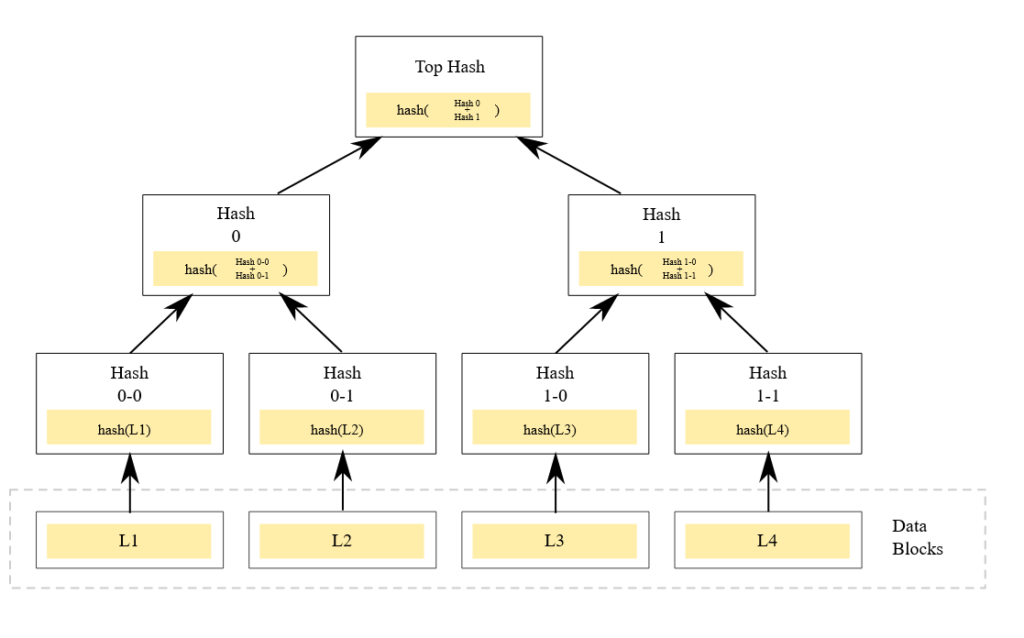
This structure is used for quick verification of the integrity of the data shared by a source. The top level hash can be shared from a trusted source and then you can validate the data integrity by checking the top hash generated by the downloaded hash tree.
If any bit of the data transmitted is modified by error or by manipulation the hash will never match with the trusted one. The trusted data is agreed by the consensus mechanism.
Timestamps
Look at the clock. What time is it? Ok you got a timestamp.
A timestamp is an encoded value that represents a time instant in a time unit. For example, 1608749743 value at the Unix timestamp would mean “1608749743 seconds since Jan 01 1970. (UTC)” and would be the same as 12/23/2020 @ 6:55pm (UTC).
In the blockchain timestamps are used to mark the moment when a transaction was done.
Consensus mechanism
So if all users are sending transactions to every node without coordination, how do we arrange what transactions are correct or not or in which order do we put them?
A criteria should be used in order to prevent fraudulent transactions, errors, double spending and to correctly sort them in order.
The Nakamoto consensus is the consensus mechanism used in the Bitcoin blockchain. It has 4 pillars:
- Proof of work
- Block selection
- Scarcity
- Incentive structure
Proof of Work (PoW)
If I tell you that to call anyone you have to do 30 pushups every time and send me a video proving it, would you call so often? That’s proof of work. You’re making the call effortful (pushups are hard), valuable (it takes your time) and easily verifiable (the video).
Technically, proof of work is a way of an user to prove to verifiers that some computational effort has been done. This proof can also be easily verified by interested parties.
Proof of work mechanism binds real world value -electricity cost- with the blockchain transactions.
Because of this, the longest chain of the network is considered the valid one as it comes from the largest computational pool. Attacking the network would then require 51% of the computing power2.
Solving PoW puzzles involves generating a hash with a value smaller than a random target. Hashcash system.
By using proof of work, mining a block (which contains transactions stored) has a significant cost and makes transactions valuables. Value by code.
Block selection
How are the blocks selected? It’s based on who solves first the block PoW. As solving the PoW is stochastic, even though more computing power gives you more chances to win the block selection, it doesn’t guarantee that you will win the next block selection.
You’re buying more tickets to a lottery but you know that no one wins the lottery just by buying more tickets.
This mechanism prevents to know who will be the next to win the block selection so you cannot pervert the system by influencing the block miners. Equality by code.
Scarcity
Value is tightly related with availability. If something is widely available is not as valuable as something that is not. This has been the traditional system for storing value. Gold standard. The exception is now due to the fractional reserve banking system.
Bitcoin is scarce. Supply is limited to 21 million. It can only be generated by mining blocks, so supply is fixed by code. This is different from established currencies where supply is controlled by central banks. Scarcity by code.
Incentive structure
So what would you be getting if you’re a node trying to break the Bitcoin network? Your Bitcoins would lose value and it will cost you a lot of electricity as you would need at least a 51% of the computing power. That’s the incentives.
As Bitcoin is scarce and generating new Bitcoins and minting transactions is expensive, it incentives the network and users to cooperate in for maintaining and securing the system.
Miners want to contribute honestly with their blocks as they will be rewarded by Bitcoins which are scarce.
Also, if nodes try to manipulate or damage the network, their Bitcoins would lose value, so they would be also punished. Skin in the game by code.
How the blockchain works
Now let’s connect the dots using the tools previously described. For that you need to know the operation flow:
- You have a unique signature (your pair of keys).
- You execute one timestamped transaction to another user which has another signature.
- This transaction is streamed over the network to all nodes.
- Nodes collect transactions into blocks.
- Nodes start trying to solve a proof-of-work, once solved, block is streamed over all nodes.
- Nodes check the validity of all transactions inside the block (including double spending) checking hashes and the Merkle tree.
- If the block is valid, they are chained together creating a record of linked blocks. For linking, it summarizes the contents creating a hash. The hash is linked in a Merkle tree.
- The block is finally stored into the current longest blockchain.
So in the end we have a big list of timestamped signed transactions grouped into blocks with a solved proof of work. Each block is summarized with a hash and blocks are chained with their hashes generating an easily verifiable Merkle tree.
Footnotes
1 Your identity could be anonymous, but you would have an unique identity that no one can impersonate.
2 51% attack allows attackers to revert transactions by regenerating the last block with other transactions. That would make dissapear the transactions of that block.
References
Background vector created by rawpixel.com – www.freepik.com
If you enjoyed this post, you can subscribe to my newsletter to receive more like this.